China’s great cannon and censorship
The recent alarm that Chinese hackers had penetrated several vital digital systems even among dissidents in other countries, such as for example Canada, shows that cyber war is becoming the norm. What happens to freedom of expression when totalitarian states by the press of a button can silence critical voices on the other side of the globe? Maria Vanta reports.
In late March, GreatFire experienced a devastating Distributed Denial of Service (DDoS) attack which took down tools that had been allowing Chinese users to access state-blocked websites. In the wake of the attack, China and its Great Firewall—a censorship tool shielding Chinese users from blocked web content like Facebook—was criticized as being behind it all. China's foreign ministry vehemently denied these accusations, claiming to be victims as much as everyone else involved.
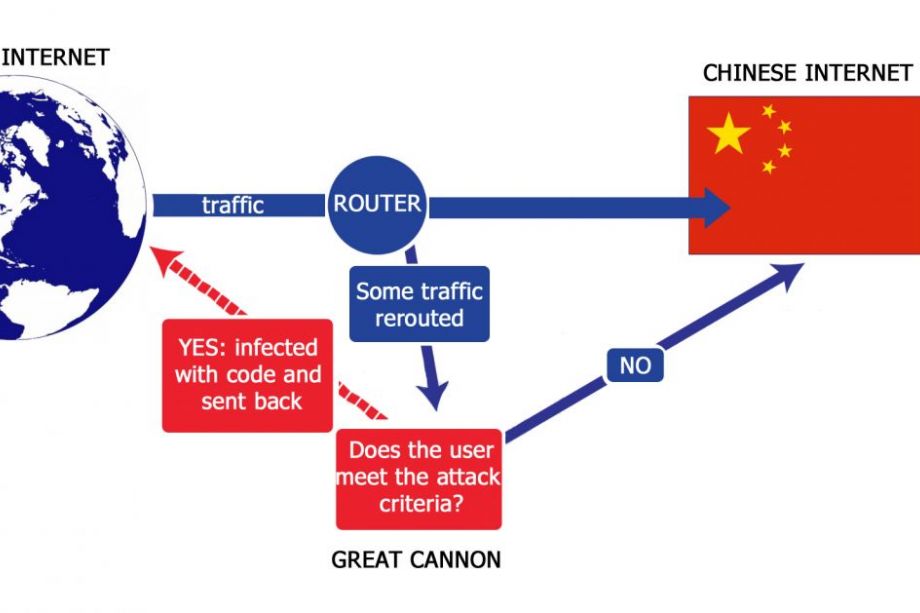
Findings from the Citizen Lab, a cyber-security think tank housed at the Munk School of Global Affairs in the University of Toronto would suggest otherwise. In a report published in April, researchers prove that China has developed an offensive cyber weapon—appropriately dubbed the Great Cannon—which intercepts foreign web traffic, injects it with malicious code and then uses it to serve Chinese interests.
In the case of GreatFire, these interests were to ensure users would no longer be able to circumvent the Great Firewall.
“The [Great Cannon] targeted random bystander computers who were visiting websites that hosted ads by the Baidu advertising network,” says John Scott-Railton, one of the authors of the report. “This meant that some subset of all the computers in the world ... got a little piece of malicious code back instead of the genuine content, which turned the computer into a bystander botnet.”
More alarmingly, a slight adjustment to the Great Cannon would make it even more dangerous.
“The second part of our finding is that the technology that China used to launch this attack could, with a technical modification, be used to remotely hack any computer that is receiving unencrypted web content from within China,” says Scott-Railton. “So it's both good for launching a massive attack as well as an extremely precise one.”
This isn't exactly new, but is instead an aggressive extension of previous cyber behaviour exhibited by the Chinese against those whom they term foreign hostile elements‑civil society, NGOs and Western journalists, to name a few.
The Chinese have always had various types of tools that have allowed them to undertake digital attacks on actors who they do not approve of or who they consider hostile. In fact, from the Chinese perspective the attack on Great Fire was likely considered to have been rather tailored and a restrained use of the Great Cannon.
“They used it as something that they're not all that concerned about the international community being aware of; it was a demonstration of capability,” says Sarah McKune, one of the authors of the report and the senior legal advisor for Citizen Lab.
The Communist Party of China (CPC) closely polices access to foreign content which may pose a threat to its ideology and legitimacy. McKune says that for the CPC, safeguarding its ideology is of the greatest concern. “They are willing to take steps to secure ideology from attacks even when those steps may undermine its economic interest or even diplomatic relations,” she says.
Thus the Great Cannon may be a tool that should be feared most for its power to reinforce state censorship and police citizen morality. In China, censorship is implemented in a number of ways, the most well known being through the Great Firewall.
“There are technical means used on a national level by bureaucratic agencies that perform and administer controls and restrictions,” says Jason Ng, a research fellow at the Citizen Lab specializing in Chinese cyber-policy. “In parallel, the propaganda and publicity department issues various directives to media companies informing them to perform certain types of specific censorship and thought leadership with regards to the content that they would like to be controlled going forward,” he says.
He points out that in past few years this type of censorship has been extended towards things related to protest, collective action and destabilizing elements, however it is not limited to this. Less politicized content like pornography and online video games are also targets. There is a history of moral content being regulated by the state going back to the 1980s with campaigns focused towards annihilating western ideas, fashion and thought.
“It also goes back to various narratives about needing to police the morality of citizens in order to ensure you have a healthy society,” says Ng. “In recent years that's focused on censoring any information thought to mislead youth and other issues believed to put in danger a stable population. They target things like trying to ensure young people don't play online games too much.”
This tightening of censorship and the ensuing crackdown on online activity that followed despite China's move towards guarded liberalization and less foreign market restriction, can be traced back to 2013. Some suggest it's linked directly to the Xi Jinping's assent to the presidency that year, though it remains unclear whether it is a transitory change.
“It's difficult to say whether this tightening of controls is a temporary thing to consolidate power for the new president,” says Ng. “It might just be a temporary thing where he is trying to stamp out online dissent in order to gain control, but it may also be a sign of how the government wants to try to control information online in the long-term.”
This recent crackdown largely centres on social media, something on which the previous presidency focused considerably less.
“[It targets] the big Vs, so called verified users who have a large number of followers,” says Ng. “There may not be a concerted effort to take down strict online content but rather the government is concerned about individuals who are non-state entities having such a large voice outside of regulated state media.”
Nevertheless, the average user can unknowingly become a pawn in cyber-warfare when accessing a seemingly innocuous website that happens to host advertisement through Baidu, a Chinese search engine. Hundreds of these unwitting bystander computers were used in the DDoS attack against GreatFire.
“When we analyzed logs from the attack ... the distribution of them tended to focus on countries with large Chinese speaking populations,” says Scott-Railton. Indeed, approximately 67% of affected users had IP addresses originating in Taiwan and Hong Kong.
This does not mean that China does not have the capacity to target foreign state actors, NGOs or any other entities they wish. Despite China's clear capacity to launch into a full-scale cyber attack, Ng points out that this is tactically unlikely.
“It's not even a technical issue it's a matter of policy and strategy whether they would actually go about doing something like that,” he says. “They have to think of what the advantages would be for them to do so thus it's not likely that the capability shown in the Great Cannon will be fully relied on unless they were at serious impasse with the US and the West,” says Ng.
He points out that the US has capacities similar to china's Great Cannon, but argues that if the status quo remains the same, neither China nor the US nor any other country that has these capabilities would go about exercising them fully because it would hugely jeopardize diplomatic relationships.
The Citizen Lab findings also importantly add to the international narrative surrounding the parameters governing cyber-space and cyber-attacks—parameters which at present are still too vague.
“Better defining the rules surrounding cyber engagement and warfare is crucial,” says a former US Defence Department staffer who asked to remain anonymous. “Otherwise, cyber intrusion and espionage will most certainly continue at its current pace, though it is unlikely that it will take the form of full scale cyber warfare unless there is a big shift.”
McKune also suggests that there has to be more discussion not only around economic consequences, industrial espionage and attacks against infrastructure, but also around attacks against people exercising their internationally recognized human rights
“[These are] becoming more and more common,” she says. “There needs to be more dialogue specifically focused at this question and the creation of appropriate norms and frameworks for the protection of civil society.”
At present, there are several steps that Western users should take to decrease the chance of becoming compromised. Unencrypted traffic is inherently vulnerable thus it is necessary that use of encrypted traffic streams becomes the norm. Encryption tools and more robust security in general is essential to protecting oneself from malicious attacks—and in this case can also indirectly help in the fight against state enforced censorship.
“People who are network engineers need to think about ways of mitigating—how do we prevent a nation from injecting this type of malicious code,” says Ng. “On the strategic front it's a matter of ensuring that there is an open line of communication between military, the state department and the diplomatic corps so that there is no misleading reading and escalation of the situation.”
Maria Vanta is a freelance writer based out of Toronto, Canada. Her background is in criminology which allows her to cover a wide breadth of topics ranging from organized crime and corruption to cyber security and policing.

